Samsung mobile devices need to be protected against the many cyber security threats that exist today. These Android-based smartphones and tablets can be compromised in several ways, whether through malicious action on the part of hackers or unintentional consequences due to user error. This guide provides a comprehensive list of practices to adopt to completely secure a Samsung mobile device.
Mobile Device Management
Mobile device management solutions offer features such a finding the phone if it's lost and remotely wiping it. In the event that the device gets lost or stolen, this type of application gives a person control over their data's exposure. While it can be frustrating to completely wipe a phone, especially if it's later found, it's better than having sensitive data falling into someone else's hands. The average person has a significant portion of their digital life on their mobile devices. Think about the damage that could be done when a criminal can access bank accounts.
Protect Internet Browsing
Trying to maintain privacy when browsing the Internet is a frustrating endeavor. Countless companies are tracking many details about Internet users, from their locations to the webpages that they look at. Over time, these companies build up usage profiles that they use for advertising and other purposes. In some countries, the government or law enforcement agencies will track internet usage to spy on people and censor information. Get a free and open Internet with protected and private browsing through the use of a Virtual Private Network service.
A VPN is a type of technology that encrypts browsing data and makes it difficult for someone to determine the user's identity. These services accomplish this goal in several ways. The first is that all of the user's browsing sessions pass through the servers that the VPN service controls. The connection is encrypted so even if a hacker accesses the data somehow, they're not capable of getting any useful information from it. VPN solutions often have servers all over the world, so this tool is useful for other reasons as well. For example, if a person wants to watch content on Netflix that is region locked to a different country, it's a simple matter to choose that country's servers from the list. As far as Netflix knows, the person is located in that country when they access the video and are able to watch it. Take a look at this this good Android VPN and its features list.
Improve Password Complexity
Databases with millions of passwords are available on the Dark Web and other criminal resources. Many people opt to use the same password on multiple websites or only use slight variations of the same password over time. Hackers use automated systems for trying out compromised usernames and passwords, inputting the information to many websites to determine whether it's a valid combination. Use a strong password that includes varying capitalization, special characters, and numbers to make it much more difficult to figure out. If a person receives a notification that their information is available on the Dark Web, then they need to immediately change their password. Otherwise, changing passwords every month to three months will help maintain security.
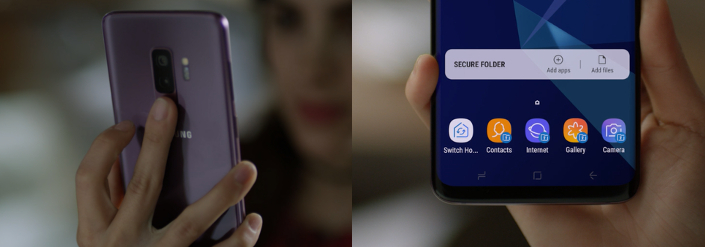
Use More Than One Authentication Factor
A username and password combination is one form of authentication that people use to access applications and websites through their Samsung mobile device. However, a single-factor authentication is not sufficient protection in today's cyber crime-filled world. Two-factor or multi-factor authentication incorporates other ways of verifying that the person is who they say they are. For example, biometric authentication looks at a person's face, fingerprints, or eyes to determine their identity. Physical authentication hardware is another way of securing smartphones and tablets.
Create a Passcode on the Lock Screen
Your Samsung mobile's lock screen should never be left unlocked. If someone were to pick up the phone and take it, they would be able to immediately access the data that's available on the device. The lock screen settings are available under the Security section in the Android operating system settings. There are several ways to secure this screen, such as by setting a password or a numerical code. Users can also control how much information is shown on the lock screen. For example, instant messages from chat software may simply show that a notification has arrived, or it can show the content of the message. For maximum security, limit the amount of information on the lock screen.
Use an Anti-malware App
Samsung mobile devices can get viruses and other malware just like a computer can. Anti-malware software is available for mobile platforms, and they work to protect the device against malicious software. In most cases, this type of application runs in the background and only notifies users if there's any activity that they need to be aware of. If malware is detected, the software quarantines the files and stops them from damaging the phone's operation and data.
Avoid Public Wi-Fi Hotspots
Public Wi-Fi hotspots are convenient but they're also quite hazardous from a security standpoint. Opportunistic hackers can use the shared network to try to break into people's devices or watch their data as they browse. Avoiding this type of connection is the best way to limit the risk, but VPN users do enjoy protection against this type of attack as well. Since all of their data is encrypted, the cyber criminal can't get access to any of that information.
Keep on top of Updates
The Android operating system and the applications running on it have frequent updates that need to be applied. For applications, the Google Play store typically pushes out the latest updates so all apps are kept on the latest version. However, if someone sets their phone to only update apps on Wi-Fi and then never connects to a Wi-Fi network, then they may be missing out on these updates. Double-check that they're getting put on the phone. For operating system updates, check in the About section of the Android system settings frequently if the phone's carrier doesn't push out the updates over the air.
Scrutinize App Downloads
Applications are not always what they appear to be, especially if they're downloaded from sources other than the Google Play app store. Double-check user reviews and other sources to determine whether an application is on the up and up. In some cases, they are malware in disguise and can create many problems for the Samsung mobile device. If an application is doing something odd and unexpected, it's a good idea to uninstall the application and do some research about it online. Sometimes it's an innocent bug that's causing a problem, but in other cases, it's malware that is putting the entire Samsung device at risk.
Learn More About Cyber Security
One of the best ways to stop cyber criminals from ruining one's day is to learn as much as possible about the potential cyber threats that exist today. Many of the attacks rely on some form of social engineering, which means that they manipulate people into taking the actions the attackers want. Phishing emails are a prime example of social engineering that most people encounter in a personal or professional capacity. By improving cyber security literacy, mobile devices owners take concrete steps against the hackers. Local community colleges often have this type of training available, and countless online resources also have the information. Some businesses will bring in cyber security trainers for their employees and take them through workshops to better understand what's going on with their devices and systems.
Make Frequent Backups
The possibility of wiping a phone remotely in the event that it gets lost or stolen, or needing to factory reset a device that's been the victim of malware, means that a robust set of backups are needed to avoid disruption of a person's day. With the right backup solution, it's not a big deal to delete the data off of the phone. In a few minutes, they can be back up and running like nothing happened. When choosing a backup solution, make sure to test the generated backups to ensure that it restores properly before trying to do so in an emergency.
Customize App Permissions
Later versions of the Android operating system provide users with the ability to fine-tune the permissions that each application uses. During the installation process, users get prompted for the base application permissions requested. They can choose whether to allow the app to have these permissions only when the application is opened, or opt to allow the app to always have access in the background. Once the user opens up the application, they get prompted for additional permissions required as the app needs them. These permissions can be controlled at any time, making it possible to immediately revoke access to sensitive system resources such as the microphone and the camera.
Avoid Getting Access to Mobile System Files
Rooting Android phones is a method for gaining access to the operating system's files. Power users root their phones to put custom versions of operating systems on the device, use root-required applications, and to have full access to the device's files and folders. While this level of access is useful for advanced users, it also represents a serious security risk, as hackers have a much easier time getting to sensitive file locations on these systems. Unless it's absolutely necessary to root a Samsung mobile device, avoid this process for security's sake.
The number of threats facing Samsung smartphones and tablets will only rise as hackers learn new ways to break into mobile devices. By incorporating all of these practices into one's digital life, the risk of being targeted by a cyberattack is much lower than it otherwise would be.